- Contents
- Index
- A -
Apple CoreStorage/FileVault/Fusion Drive Volumes
- B -
Bad Sectors settings
Set default read retries count for all drives
Binary (byte to byte copy)
BitLocker System Drive Encryption
Broken File Name
Rename and change all invalid symbols to:
Broken File Name options
Button
Buttons
Create virtual volume sets or RAIDs
- C -
Connect to R-Studio settings
Contact information and technical support
Find Previous Versions of the File
Find Template Signature Previous
Remove All Scanned Information
Contextt menu
Create menu
Creating and saving your own RAID configuration
Creating Startup Disks for Mac and Linux Computers
- D -
Data Copy in Text/hexadecimal editor
Data Recovery on HFS/HFS+ File System
Description Files for Various RAID Configurations
Devices to Store Recovered Files
Dialog box
Dialog boxes
Edit Block RAID Layout Presets
Please configure R-Studio Agent for Mac
Please configure R-Studio Agent for Windows
R-Studio Agent for Linux Configuration
There is not enough space on the disk
Drive menu
- E -
Edit menu
Find Template Signature Previous
Editor tabs
Exclusive Region options
- F -
Fast Search for Lost Partitions
File Already Exists
File Information (R-Studio Technician/T80+)
File mask options
File menu
File Systems settings
Default encoding for Ext2/Ext3/Ext4/UFS volumes
Default encoding for HFS volumes
File Type Signature Specification
File Types
Find options
Find/Mark options
Find/mark objects only in real paths, ignore links to folders
Finding Previous File Versions
Forensic Data Collection Audit Log
- H -
Hidden Attribute
- I -
Image options
Image type:
Byte to byte image to a physical disk
Compressed image (R-Drive Image compatible)
VMDK (VmWare Virtual Machine Disk)
- K -
Known File Types settings
- L -
Log settings
Maximum messages in the Event Log
- M -
Main settings
Reset all hidden notifications
Messages
Double-click a logical disk...
- N -
Nested and Non-Standard RAID Levels
- O -
Opening several disks/partitions in one tab
Opening Virtual Disks from the Files Panel
- P -
Panels
Panes
Properties tab
- Q -
- R -
Recover options
Condense successful restoration events:
Open local folder (folders) when done
Recover alternative data streams:
Recover real folders structure
Region options
Contact information and technical support
Installing R-Studio Agent Emergency Startup Media Creator
Starting a Computer with the R-Studio Agent Emergency Startup Disk
R-Studio Agent for Mac main panel
R-Studio Agent for Windows main panel
Contact Informaiton and Technical Support
Installing R-Studio Emergency Startup Media Creator
Properties and Text/Hexadecimal Viewer
Starting a Computer with the R-Studio Emergency Startup Disks
R-Studio Emergency Startup Media Creator
- S -
Scan options
Search options
Settings
Shortcut menu
Smart drive copy
Copy all partitions onto original places
Expand/Shrink partition to whole disk
Smart partition copy
Startup Media Troubleshooting Options
Symbolic Links
Don't show symbolic links by default (Technician version)
Recovery as it is (Technician version)
Show folder symbolic links as links to their targets, without target content (Technician version)
Symbolic links display settings
Symbolic links recovery options
Syntaxis of a Description File for RAID Configurations
- T -
Tabs
Technical Information and Troubleshooting
Tools menu
- U -
- V -
Various Disk and Volume Managers
View menu
Volume Sets, Stripe Sets, and Mirrors
- W -
Window
Working with RAID 6 Presets
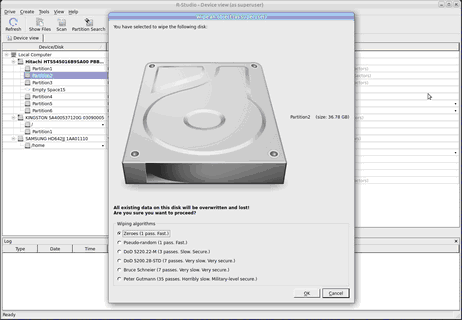
Wiping Objects
Disk objects can be wiped in order to completely destroy its data.
Supported Wipe Algorithms
File wiping is necessary only for files stored on conventional hard drives. Files stored on new SSD storage devices cannot be effectively wiped out due to the principles of operation of these devices.
Currently R‑Studio supports 6 wiping algorithms:
|
Zeroes |
The disk object or file is filled with zeroes through 1 pass. The fastest but the least secure algorithm. Also it does not conceal the fact that the disk or file has been wiped. |
|
Pseudo-random numbers |
The disk object or file is filled with pseudo-random numbers through 1 pass. A slower but little bit more secure algorithm than the Zeroes algorithm and it also conceals to some degree the fact that the disk or file has been wiped. |
|
DoD 5220.22-M(3) |
The disk object or file is wiped using Department of Defense standard 5220.22-M(3). Provides high-grade data wiping filling the unused space or file with a special digital pattern through 3 passes This algorithm is very secure, but slow. |
|
DoD 5200.28-STD(7) |
The disk object or file is wiped using Department of Defense standard 5200.28-STD(7). Provides high-grade data wiping filling the unused space or file with a special digital pattern through 7 passes. This algorithm is very secure, but very slow. |
|
Bruce Schneier(7) |
The disk object or file is wiped using the Bruce Schneier(7) algorithm. The first pass overwrites the drive with the bit pattern "00", the second with "11", and the next five with a randomly generated bit pattern. This algorithm is very secure, but very slow. |
|
Peter Gutmann (35) |
The disk object or file is wiped using the Peter Gutmann's algorithm . Provides high-grade data wiping filling the unused space or file with a special digital pattern through 35 passes. This algorithm is military-level secure, but horribly slow. |
What algorithm is to choose, depends on your specific needs. All of these wiping algorithms make recovery of wiped data with any software-based data recover utility impossible. So if you want to protect your information from a casual snooper, you may safely choose either the Zeroes or Pseudo-random numbers algorithm. The latter also conceals the fact that you wiped the data.
If you want more security , you need to know the following:
There are some techniques for recovery of wiped data. These techniques are based on the fact that magnetic medium on the hard drive's platters "store" some information about previously written data. Such information cannot be completely removed. Wiped data may be recovered even from mechanically damaged platters. So the only safe way to completely remove data from a hard drive is to mechanically grind the magnetic medium off the drive platters or dissolve them in special chemical solvents.
But in order to recover the wiped data using one of these techniques, a hard drive must be disassembled, its platters placed in a precise magnetic field measurement system, and the results of such measurement statistically processed. All that is very expensive and requires a very qualified and experienced personnel and a specially developed equipment. Only a very advanced organization such as a law enforcement or intelligence agency of a developed nation, or a special high-tech firm can afford this. Moreover, each successive wiping pass makes such data recovery much and much harder. So, the DoD 5220.22-M(3) clearing and sanitizing standard overwriting the data with a special pattern through 3 passes is a rather reliable and safe choice for this case.
If you need the ultimate security, use the DoD 5220.22-M(7) clearing and sanitizing standard, the Bruce Schneier(7) , or even the Peter Gutmann (35 ) wiping algorithms. They render data almost unrecoverable, but they are extremely slow.
Wiping Disk Objects:
To wipe a disk object,
| 1 | Right-click the disk object in the Device view pane and select Wipe... |
| > | The Wipe an object dialog box will appear. |
| 2 | Select the desired wiping algorithms and click the OK button. |
| > | R‑Studio for Linux will start wiping the object. |
- R-Studio Technician: activation using a USB stick
- Data Recovery Guide
- Why R-Studio?
- R-Studio for Forensic and Data Recovery Business
- R-STUDIO Review on TopTenReviews
- File Recovery Specifics for SSD devices
- How to recover data from NVMe devices
- Predicting Success of Common Data Recovery Cases
- Recovery of Overwritten Data
- Emergency File Recovery Using R-Studio Emergency
- RAID Recovery Presentation
- R-Studio: Data recovery from a non-functional computer
- File Recovery from a Computer that Won't Boot
- Clone Disks Before File Recovery
- HD Video Recovery from SD cards
- File Recovery from an Unbootable Mac Computer
- The best way to recover files from a Mac system disk
- Data Recovery from an Encrypted Linux Disk after a System Crash
- Data Recovery from Apple Disk Images (.DMG files)
- File Recovery after Re-installing Windows
- R-Studio: Data Recovery over Network
- How To Use R-Studio Corporate Package
- Data Recovery from a Re-Formatted NTFS Disk
- Data Recovery from an ReFS disk
- Data Recovery from a Re-Formatted exFAT/FAT Disk
- Data Recovery from an Erased HFS Disk
- Data Recovery from an Erased APFS Disk
- Data Recovery from a Re-Formatted Ext2/3/4FS Disk
- Data Recovery from an XFS Disk
- Data Recovery from a Simple NAS
- How to connect virtual RAID and LVM/LDM volumes to the operating system
- Specifics of File Recovery After a Quick Format
- Data Recovery After Partition Manager Crash
- File Recovery vs. File Repair
- Data Recovery from Virtual Machines
- How to Recover Files from a Remote Computer Using R-Studio Standalone License and Its Network Capabilities in Demo Mode
- How to Connect Disks to a Computer
- Emergency Data Recovery over Network
- Data Recovery over the Internet
- Creating a Custom Known File Type for R-Studio
- Finding RAID parameters
- Recovering Partitions on a Damaged Disk
- NAT and Firewall Traversal for Remote Data Recovery
- Data Recovery from an External Disk with a Damaged File System
- File Recovery Basics
- Default Parameters of Software Stripe Sets (RAID 0) in Mac OS X
- Data Recovery from Virtual Hard Disk (VHD/VHDX) Files
- Data Recovery from Various File Container Formats and Encrypted Disks
- Automatic RAID Parameter Detection
- IntelligentScan Data Recovery Technology
- Multi-pass imaging in R-Studio
- Runtime Imaging in R-Studio
- Linear Imaging vs Runtime Imaging vs Multi-Pass Imaging
- USB Stabilizer Tech for unstable USB devices
- Joint work of R-Studio and PC-3000 UDMA hardware
- Joint work of R-Studio and HDDSuperClone
- R-Studio T80+ - A Professional Data Recovery and Forensic Solution for Small Business and Individuals Just for 1 USD/day
- Backup Articles
- R-Drive Image Standalone and Corporate license transferring
- Fixing Windows update error 0x80070643 with R-Drive Image
- Backup with Confidence
- R-Drive Image as a free powerful partition manager
- Computer Recovery and System Restore
- Disk Cloning and Mass System Deployment
- Accessing Individual Files or Folders on a Backed Up Disk Image
- R-Drive Image startup / bootable version
- File Backup for Personal Computers and Laptops of Home and Self-Employed Users
- Creating a Data Consistent, Space Efficient Data Backup Plan for a Small Business Server
- How to Move the Already Installed Windows from an Old HDD to a New SSD Device and Create a Hybrid Data Storage System
- How to Move an Installed Windows to a Larger Disk
- How to Move a BitLocker-Encrypted System Disk to a New Storage Device
- How to backup and restore disks on Linux and Mac computers using R-Drive Image
- R-Drive Image and Virtual Machines
- Undelete Articles
- Get Deleted Files Back
- Free Recovery from SD and Memory cards
- R-Undelete: Video Recovery
- Recovery from an External Device with a Damaged File System
- File recovery from a non-functional computer
- Free File Recovery from an Android Phone Memory Card
- Free Photo and Video File Recovery Tutorial
- Easy file recovery in three steps