-
Data Recovery from Various File Container Formats and Encrypted Disks
R-Studio is designed to recover data from physical hard drives and other media. But it can also be used to recover files that have been stored in virtual disks or file container formats. File containers often include all the same parts of a real disk-including a boot record, disk partitions, file systems and individual files and folders. File containers can be uncompressed, compressed or encrypted. In addition, there are utilities that can encrypt an entire disk.
The method for recovering data from a file container depends on its format. This article covers data recovery methods using R-Studio for the most common file container formats.
Types of File Containers with Disk Images
There are several types of file container formats that function as disk images:
- File containers from virtual machines - These are file container formats that are meant to be mounted by a virtual machine, such as a VirtualBox or VMware. Most of them can be loaded directly in R-Studio and processed as real physical drives or logical disks/partitions.
- Uncompressed disk images - This is a sector-by-sector copy of a disk created from a logical volume or an entire physical drive. This type of disk image can be loaded into R-Studio and processed like any other image.
- Proprietary file containers - Some utilities use their own disk image formats. R-Studio supports many of such formats, and can load them to process like real disks - including supported disk image format from R-Drive Image, or backup and copying utility developed by R-TT, Inc. that creates file containers with the .rdr file extension. There are several other formats that R-Studio supports, too.
- Encrypted file containers - These are similar to proprietary file containers, but the contents are also encrypted. R-Studio can unlock some of them, or they can be mounted and read by the original software used to create the image. Either way, it can be detected by R-Studio and processed like a normal logical disk.
File Containers from Virtual Machines
Our article Data Recovery from Virtual Machines describes the best method for recovering files from virtual disks created by most popular virtual machine software. There's another one of our articles, Data Recovery from Virtual Hard Disk (VHD/vhdx) Files discussing data recovery from the most popular virtual disk format.
Uncompressed Disk Images
Uncompressed disk images can be loaded directly into R-Studio and processed accordingly.
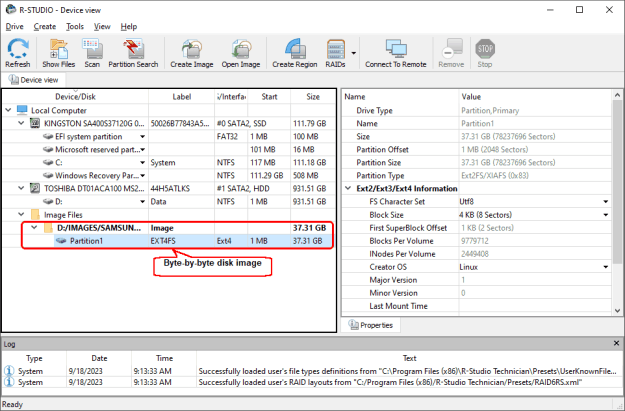
Fig.1: An Uncompressed Disk Image in R-Studio
Click image to enlarge
See the R-Studio's help: Image for more details. Moreover, such images can be mounted in the host system as virtual disks to process them with another software.
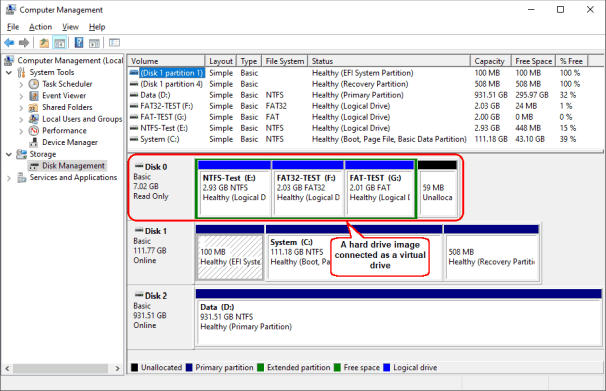
Fig.2: A Hard Drive Image Mounted as a Virtual Drive
Click image to enlarge
Such virtual drives remain mounted even when R-Studio is closed.
Proprietary File Container Formats
In addition to many virtual machine disk formats, R-Studio supports some other file containers: .dmg (an Apple virtual disk format), .rdr (a native R-TT disk image format), and .iso (an optical disc image format). They can be directly loaded into R-Studio and processed accordingly.
Data recovery from the Apple virtual disk format is discussed in our article Data Recovery from Apple Disk Images (.DMG files).
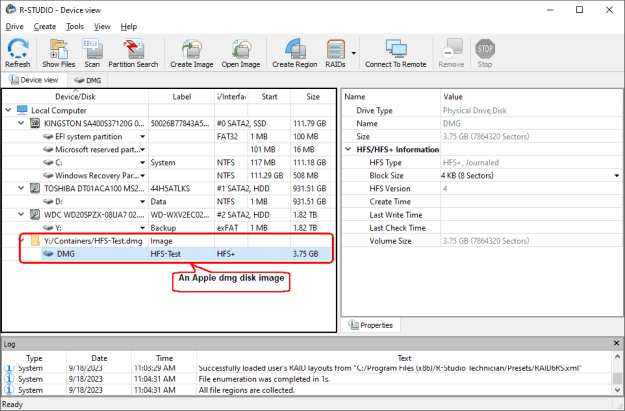
Fig.3: An Apple dmg disk image opened in R-Studio
Click image to enlarge
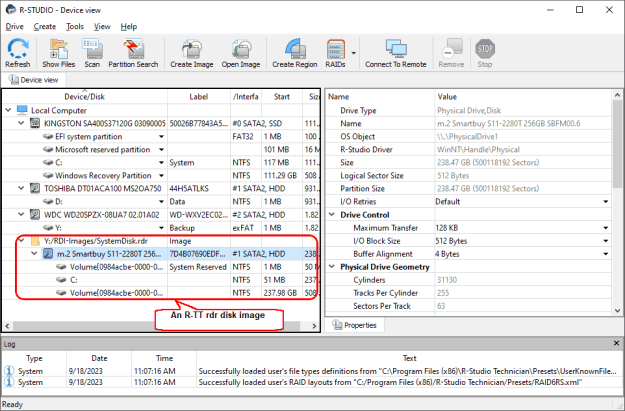
Fig.4: An R-TT rdr image loaded into R-Studio
Click image to enlarge
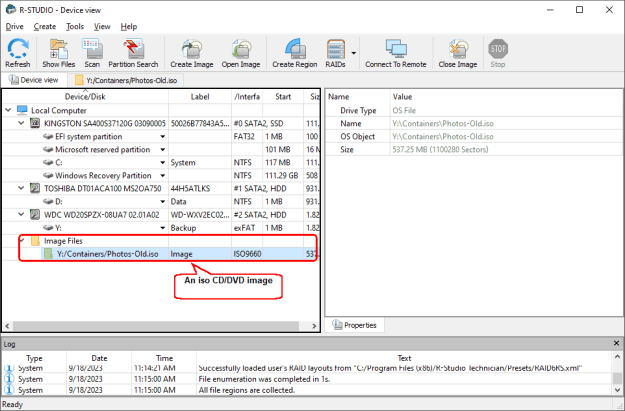
Fig.5: An iso CD/DVD image opened in R-Studio
Click image to enlarge
In addition, R-Studio Technician/T80+ can load disk images in the e01/ewf (Expert Witness) and aff (Advanced Forensic) file formats.
Note that if a proprietary file container is corrupted to the point that it cannot be connected using its native software, R-Studio can still load it as an uncompressed image and attempt to process it. However, in these cases, chances are small that useful data can be found, especially if the image is compressed.
Encrypted Hard Disks, Partitions, and Their Images
For file recovery from an Encrypted Linux Disk, read our article: Data Recovery from an Encrypted Linux Disk after a System Crash.
While images of encrypted disks are not technically the same as the disks themselves, data recovery from a disk with full disk encryption is similar to recovering data from an encrypted file container.
Data recovery from supported encrypted disks and their images
R-Studio can unlock supported encrypted disks and their images.
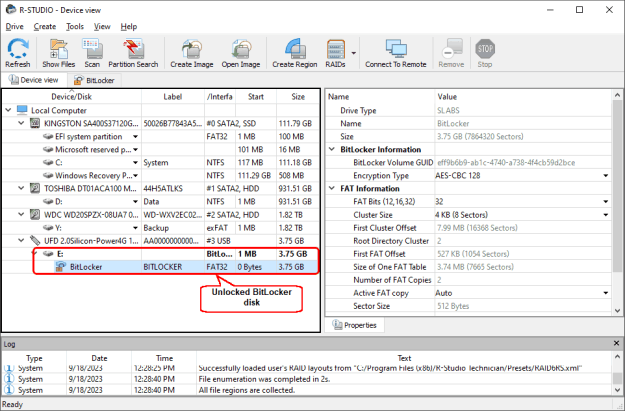
Fig.6: A BitLocker disk unlocked in R-Studio
Click image to enlarge
You may read more about working with BitLocker disks in R-Studio help: BitLocker Drive Encryption.
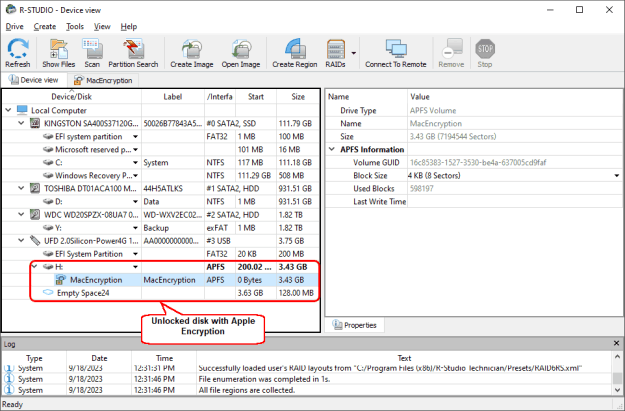
Fig.7: A disk with Apple Encryption unlocked in R-Studio
Click image to enlarge
You may read more about working with Apple Encryption in R-Studio help: Apple CoreStorage/FileVault/Fusion Drive Volumes.
Data recovery from unsupported encrypted disks and their images
If R-Studio doesn't support a particular disk encryption format, an encrypted disk can be mounted by its native software (usually using a decryption key). It will mount its file containers as virtual logical disks and provide background data encryption/decryption. These virtual disks appear in the R-Studio Drives pane as logical disks and can be processed as such.
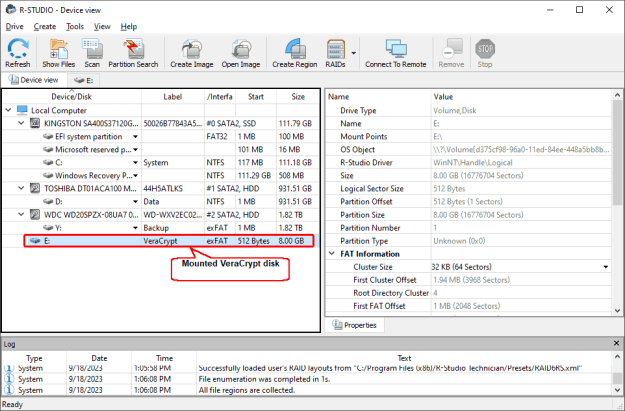
Fig.8: A Mounted VeraCrypt Disk in R-Studio
Click image to enlarge
Note that if the data on an encrypted disk is damaged so severely that it cannot be unlocked using either R-Studio or its native software, it's unlikely that any data can be recovered from it. Scanning them reveals nothing.
Conclusion
There are numerous different file container formats, most of which can be processed by R-Studio for data recovery. Uncompressed disk images, virtual machine images, and some other image formats can be loaded directly. For data recovery from encrypted disks and images or proprietary file container formats, R-Studio can unlock them - either on its own or by processing them as normal logical volumes after they are mounted in the native software. However, if the file container format is corrupted to the point that it cannot be mounted, the chance of recovering any data is minimal.
- R-Studio Technician: activation using a USB stick
- Data Recovery Guide
- Why R-Studio?
- R-Studio for Forensic and Data Recovery Business
- R-STUDIO Review on TopTenReviews
- File Recovery Specifics for SSD devices
- How to recover data from NVMe devices
- Predicting Success of Common Data Recovery Cases
- Recovery of Overwritten Data
- Emergency File Recovery Using R-Studio Emergency
- RAID Recovery Presentation
- R-Studio: Data recovery from a non-functional computer
- File Recovery from a Computer that Won't Boot
- Clone Disks Before File Recovery
- HD Video Recovery from SD cards
- File Recovery from an Unbootable Mac Computer
- The best way to recover files from a Mac system disk
- Data Recovery from an Encrypted Linux Disk after a System Crash
- Data Recovery from Apple Disk Images (.DMG files)
- File Recovery after Re-installing Windows
- R-Studio: Data Recovery over Network
- How To Use R-Studio Corporate Package
- Data Recovery from a Re-Formatted NTFS Disk
- Data Recovery from an ReFS disk
- Data Recovery from a Re-Formatted exFAT/FAT Disk
- Data Recovery from an Erased HFS Disk
- Data Recovery from an Erased APFS Disk
- Data Recovery from a Re-Formatted Ext2/3/4FS Disk
- Data Recovery from an XFS Disk
- Data Recovery from a Simple NAS
- How to connect virtual RAID and LVM/LDM volumes to the operating system
- Specifics of File Recovery After a Quick Format
- Data Recovery After Partition Manager Crash
- File Recovery vs. File Repair
- Data Recovery from Virtual Machines
- How to Recover Files from a Remote Computer Using R-Studio Standalone License and Its Network Capabilities in Demo Mode
- How to Connect Disks to a Computer
- Emergency Data Recovery over Network
- Data Recovery over the Internet
- Creating a Custom Known File Type for R-Studio
- Finding RAID parameters
- Recovering Partitions on a Damaged Disk
- NAT and Firewall Traversal for Remote Data Recovery
- Data Recovery from an External Disk with a Damaged File System
- File Recovery Basics
- Default Parameters of Software Stripe Sets (RAID 0) in Mac OS X
- Data Recovery from Virtual Hard Disk (VHD/VHDX) Files
- Data Recovery from Various File Container Formats and Encrypted Disks
- Automatic RAID Parameter Detection
- IntelligentScan Data Recovery Technology
- Multi-pass imaging in R-Studio
- Runtime Imaging in R-Studio
- Linear Imaging vs Runtime Imaging vs Multi-Pass Imaging
- USB Stabilizer Tech for unstable USB devices
- Joint work of R-Studio and PC-3000 UDMA hardware
- Joint work of R-Studio and HDDSuperClone
- R-Studio T80+ - A Professional Data Recovery and Forensic Solution for Small Business and Individuals Just for 1 USD/day
- Backup Articles
- R-Drive Image Standalone and Corporate license transferring
- Fixing Windows update error 0x80070643 with R-Drive Image
- Backup with Confidence
- R-Drive Image as a free powerful partition manager
- Computer Recovery and System Restore
- Disk Cloning and Mass System Deployment
- Accessing Individual Files or Folders on a Backed Up Disk Image
- R-Drive Image startup / bootable version
- File Backup for Personal Computers and Laptops of Home and Self-Employed Users
- Creating a Data Consistent, Space Efficient Data Backup Plan for a Small Business Server
- How to Move the Already Installed Windows from an Old HDD to a New SSD Device and Create a Hybrid Data Storage System
- How to Move an Installed Windows to a Larger Disk
- How to Move a BitLocker-Encrypted System Disk to a New Storage Device
- How to backup and restore disks on Linux and Mac computers using R-Drive Image
- R-Drive Image and Virtual Machines
- Undelete Articles
- Get Deleted Files Back
- Free Recovery from SD and Memory cards
- R-Undelete: Video Recovery
- Recovery from an External Device with a Damaged File System
- File recovery from a non-functional computer
- Free File Recovery from an Android Phone Memory Card
- Free Photo and Video File Recovery Tutorial
- Easy file recovery in three steps
Rating: 4.8 / 5
R-TT may not be the easiest or most user-friendly solution, but the algorithm used for the renaming saved me THOUSAND of hours of opening ...